Authorization process
Nuance Mix uses the OAuth 2.0 protocol for authorization.
There are two integration points that require authorization in Mix:
- Runtime environment: To access the ASR, NLU, Dialog, and TTS runtime services as well as runtime event logs, applications provide an access token created using client credentials generated from the Mix dashboard Manage tab.
- Tooling environment: To access the Mix tooling environment, applications provide an access token created using client credentials generated from the Mix dashboard Profile page.
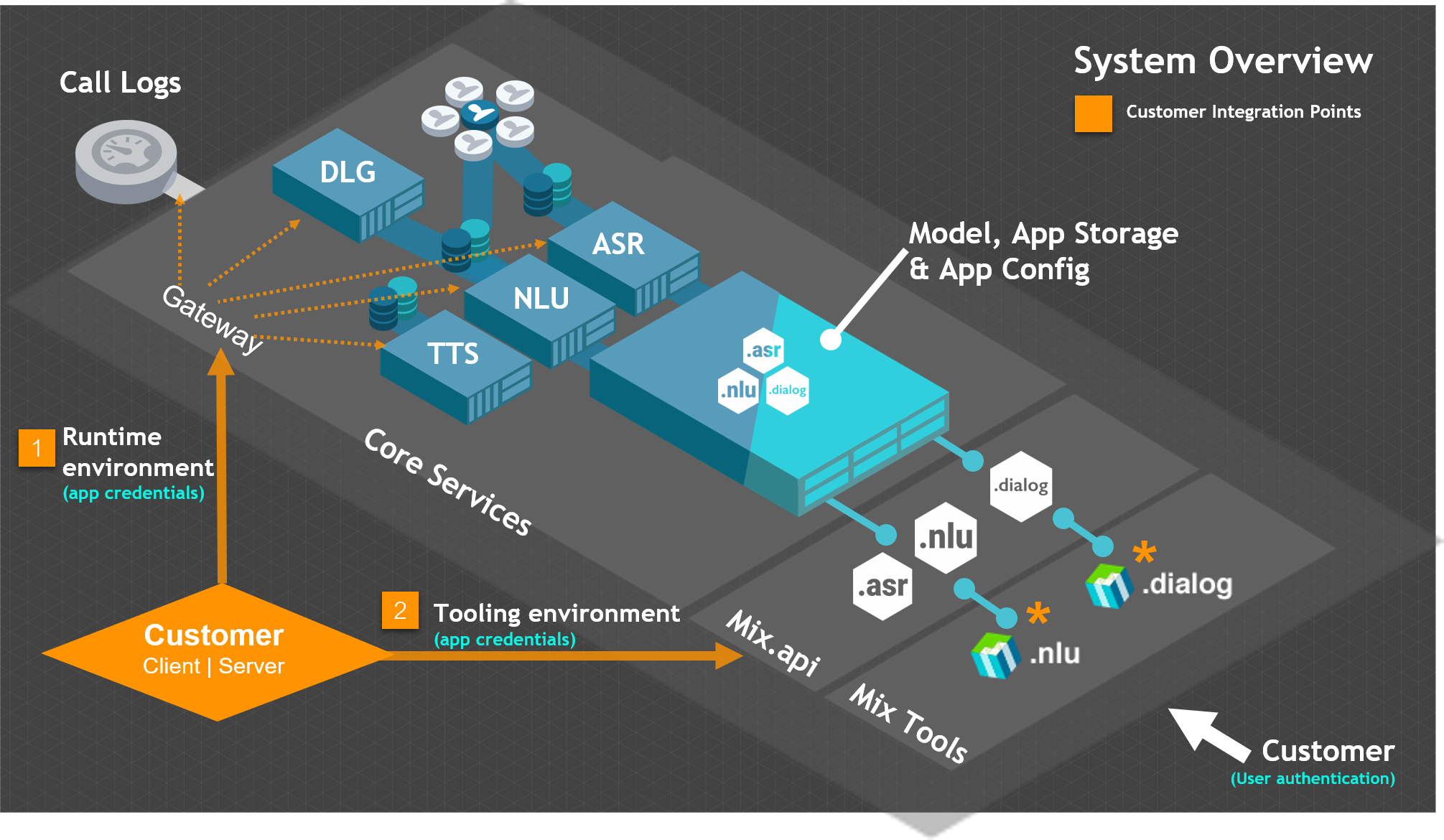
As per the OAuth 2.0 standard, there are two important concepts related to authorization: Scopes and Client credentials.
Scopes
Scope is an OAuth 2.0 mechanism that determines what information the authorized application has access to. In Mix, these scopes are available:
| Service | Scopes |
|---|---|
| ASRaaS | asr: Provides access to the ASRaaS runtime API and resourcesasr.wordset: Allows client applications to upload ASR wordsetsasr.forgetme: Allows client applications to remove speaker profiles |
| NLUaaS | nlu: Provides access to the NLUaaS runtime API and resourcesnlu.wordset: Allows client applications to upload NLU wordsets |
| DLGaaS | dlg: Provides access to the DLGaaS runtime API and resources |
| TTSaaS | tts: Provides access to the TTSaaS runtime API and resources |
| Neural TTSaaS | tts: Provides access to the Neural TTSaaS runtime API and resources |
| NRaaS | nr: Provides access to the NRaaS runtime API and resources |
| Event logs | log: Provides access to event logs |
Client credentials
Client credentials consist of a client ID and a client secret. The client credentials to use depend on the integration point.
Access to runtime services and logs
To access the runtime services and logs, client applications must provide a valid access token that is created using credentials generated from the Mix dashboard Manage tab.
These credentials (that is, the client ID and client secret) are linked to an application ID, which identifies an environment in a Mix application. For example, consider the Mix application “My Omni-Channel Application”, which has two environments: DEV and PROD:
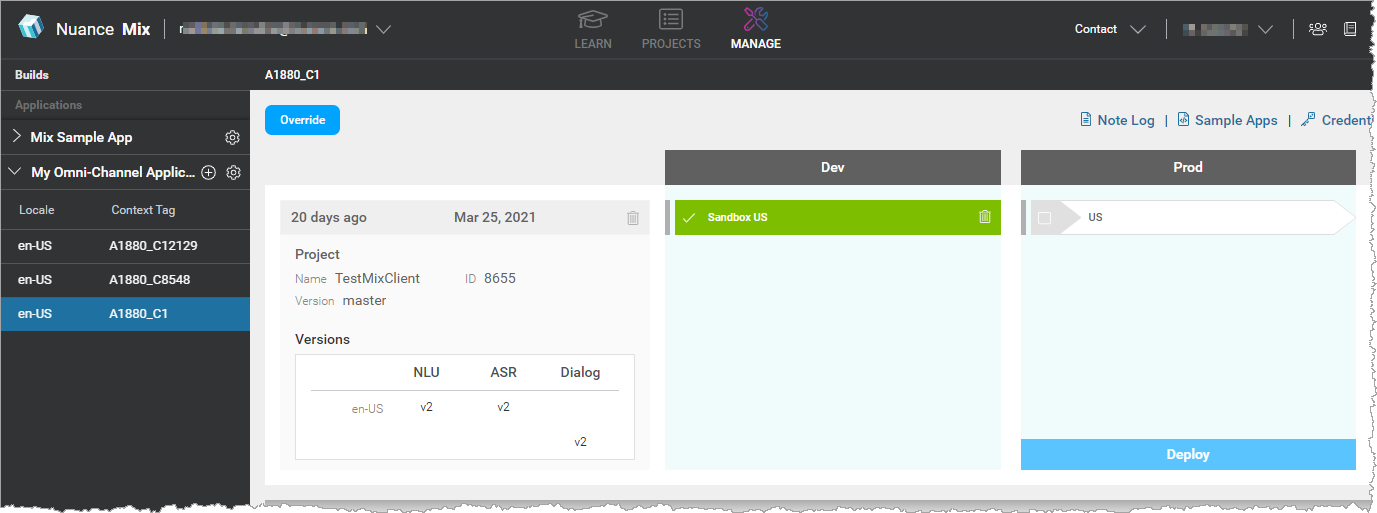
Each environment has its own app ID: DEMO-OMNICHANNEL-APP-DEV and DEMO-OMNICHANNEL-APP-PROD, and each app ID has its own set of client credentials.
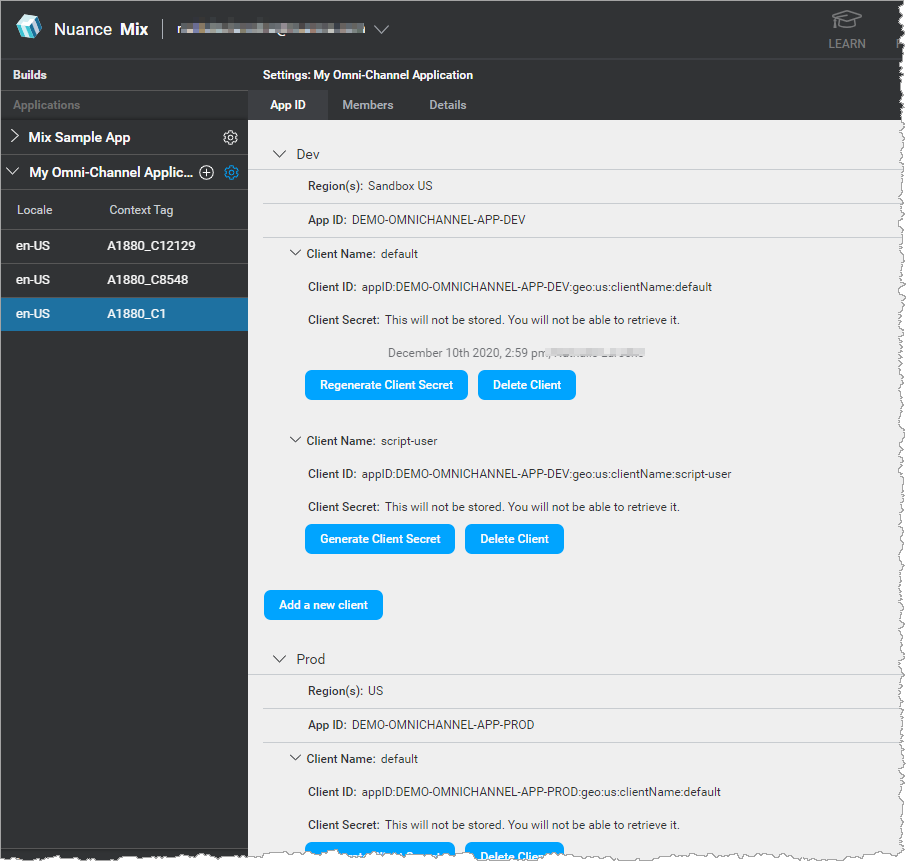
Because client credentials are linked to an app ID, they provide access to the resources associated to this app ID.
Client IDs for the runtime environment can use the scopes defined in Scopes.
The information that the application will have access to depends on the combination of the scope and client ID used to create the access token. For example:
- If an application requests an access token for client ID
appID:DEMO-OMNICHANNEL-APP-PROD:geo:us:clientName:defaultwith scopedlg, this access token will allow the application to use the DLGaaS API and access the resources that were deployed for theDEMO-OMNICHANNEL-APP-PRODapp ID. - If an application requests an access token for client ID
appID:DEMO-OMNICHANNEL-APP-DEV:geo:us:clientName:defaultwith scopelog, this access token will allow the application to use the reporting API and access the call logs for theDEMO-OMNICHANNEL-APP-DEVapp ID.
The runtime services and log use the OAuth 2.0 Client Credentials grant type flow. See Authorize your client application: Runtime for information on creating client credentials and access tokens for the runtime environment.
Access to tooling API (Mix.api)
To access the Mix.api endpoints and tooling resources, client applications must provide an access token that is created using credentials generated from the Mix dashboard Profile tab.
These credentials (that is, the client ID and client secret) are linked to a user’s account and provide the same permissions of that user.
There are two types of accounts to access the tooling API:
- A user account, which is intended for user-to-service use cases. This account uses the OAuth 2.0 Authorization Code grant type flow.
- A service account, which is used for machine identity and is intended for service-to-service use cases. This account uses the OAuth 2.0 Client Credentials grant type flow.
Client IDs created from the Profile tab use the mix-api scope.
See Authorization for information on creating client credentials and access tokens for the tooling environment.
Summary
This table summarizes the authorization options in Mix.
| Runtime environment | Tooling environment: User account |
Tooling environment: Service account |
|
|---|---|---|---|
| OAuth 2.0 Authorization type | Client Credentials | Authorization Code | Client Credentials |
| Credentials created from | Manage tab | Profile tab | Profile tab |
| Credentials linked to | App ID | User account | User account |
| Supported scopes | See Scopes | mix-api |
mix-api |
| Documentation | Authorize your client application: Runtime | Mix.api OAuth 2.0 Authorization Code flow | Mix.api OAuth 2.0 Client Credentials flow |
Feedback
Was this page helpful?
Glad to hear it! Please tell us how we can improve.
Sorry to hear that. Please tell us how we can improve.